With the spread of Covid-19 throughout the world, millions of people have moved to remote work. Whilst not everybody has enjoyed working from home, a large percentage of people have seen the benefits of doing so.
The way we work has now changed forever. Many businesses have realised that they don’t require their entire workforce to be office based and that flexible, remote working can drive and accelerate productivity.
Enabling a team to work remotely however is an ongoing challenge that looks different for every organisation, depending on their size, industry, and stage of digital transformation. Every business needs to define their own priorities to enable remote productivity across their organisation’s workforce.
To accommodate this change in the new world of work, organisations need to rethink their security model. They require a security model that effectively adapts to the complexity of the modern environment and embraces the mobile workforce which has now become the normal for many businesses and will continue to be post pandemic. It must protect people, devices, applications, and data wherever they are located.
Start with Zero Trust
Never trust, always verify
It is important to start your new security model with ‘zero trust’, based on the principle of never trust, always verify.
Each access request should be treated as though it originated from an uncontrolled network. Every access request should be strongly authenticated, authorised within policy constraints, and inspected for anomalies before access is granted. Everything from the user’s identity to the application’s hosting environment is used to verify the request and prevent breach.
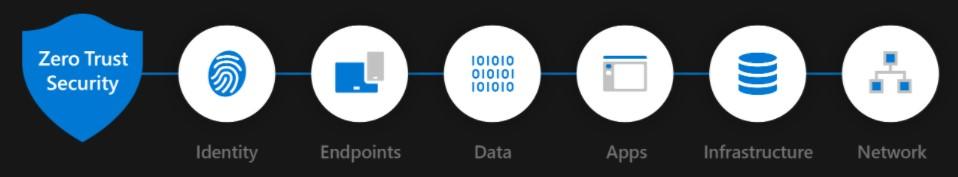
Transitioning to Zero Trust is a multi-layered journey that can take time to achieve a high level of maturity. Many security vendors however have designed frameworks to assist your business on this journey and are aligned to maturity models to track your progress. Most follow very similar principles and are based on several foundational pillars that assist in protecting your business end-to-end, covering: Identity, Endpoints, Data, Apps, Infrastructure and Network. Each of these pillars are critical elements that need to be protected.
Managing Identity
The current pandemic has seen an explosion of cloud application adoption and the mobile workforce which has significantly redefined the security perimeter. Data is being accessed outside the corporate network, so it is no longer feasible to rely on traditional network controls. These controls need to move to where the data is: on devices and inside apps.
A strong identity foundation makes it possible for users to securely access the resources and apps they need, from wherever they are.
But first, what is an identity?
An identity can represent a person, a user, it can be a service or an Internet of things (IOT) device. Manging identities is one of the most powerful ways to control access to data.
In a Zero Trust security model, before an identity attempts to access a resource, organisations need to:
- Verify the identity with strong authentication
- Ensure access is compliant and typical for that identity
- Follow least privilege access principles
Using tools such as Microsoft’s Azure Active Directory can provide a single identity management platform, allowing you to easily enable Multi-Factor Authentication (MFA). MFA safeguards users credentials and gives you that additional layer of protection and with biometric technologies almost becoming standard on the devices we use today.
Conditional Access enables organisations to create risk-based policies applied to user, device or location to determine whether access to apps or data should be allowed, limited, or blocked. Providing users with a Single-Sign On (SSO) experience encourages tougher security measures as users don’t have to have different passwords to access all of the different apps they need whether they are using SaaS or on-premise apps.
Managing Devices
Unmanaged devices are a very attractive and powerful entry point for malicious parties, and it’s vital that only authorised and healthy devices can access applications and data. With more employees working from home and across devices, organisations need a strategy to support bring-your-own-device (BYOD) scenarios.
There are a few key rules for securing devices and endpoints in a Zero Trust model:
- Zero Trust security policies are centrally enforced through the cloud and cover endpoint security, device configuration, app protection, device compliance, and risk posture.
- The platform as well as the apps that run on the devices are securely provisioned, properly configured, and kept up to date.
- There is automated and prompt response to contain access to corporate data within the apps in case of a security compromise.
- The access control system ensures that all policy controls are in effect before the data is accessed
As mentioned above, Conditional Access plays a big role in protecting your organisation from the threat posed by unauthorised devices. Using risk-based policies, devices that don’t meet the required conditions are denied access.
Many tools exist to manage these external devices and ensure that enrolled devices have the right policies applied, for example that the device is encrypted with strong passwords and anti-virus is up to date etc.
As your organisation embraces the new world of work, it is important to rethink your security requirements, protecting your people, devices, applications and data no matter where they are located. A Zero Trust security model will enable you to manage your user’s identity and devices, protecting your critical elements and driving and accelerating productivity.
 Author: James Solomon, Partner Alliance Manager, C5 Alliance
Author: James Solomon, Partner Alliance Manager, C5 Alliance















